Before starting, big shout out to Eric Zimmerman (https://github.com/EricZimmerman/) for creating so many great free DFIR tools.
KAPE can be downloaded here: https://www.kroll.com/en/insights/publications/cyber/kroll-artifact-parser-extractor-kape
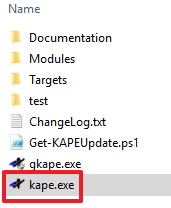
KAPE is a standalone program that does not need to be installed. Decompress the zip file to a directory of your choosing and you are ready to go. KAPE requires administrator rights when run (luckily Carbon Black Live Response runs as SYSTEM). Once KAPE is unzipped, the following files and directories will be available:
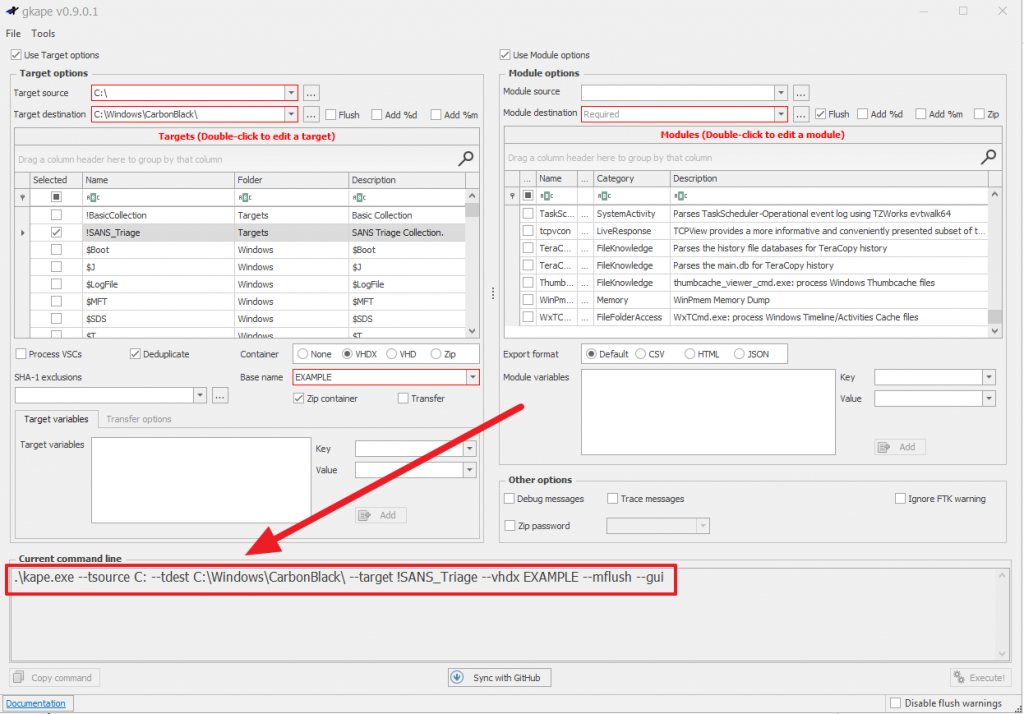
If you’re new to using KAPE, start with gkape.exe (GUI version) to help build the command line for you:
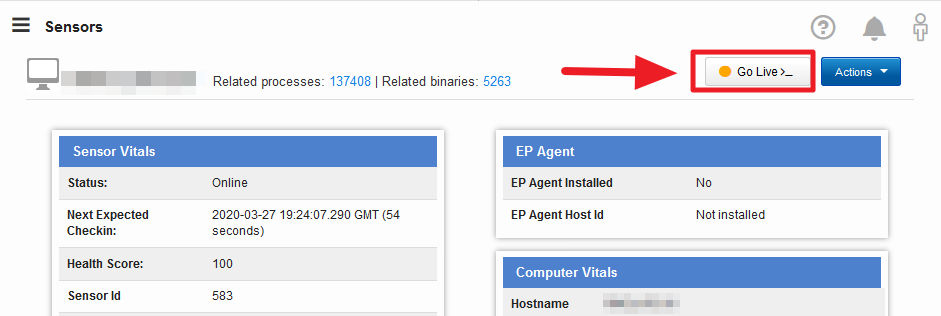
Log into Carbon Black and go to the endpoint/sensor of the suspect system.
Click the “Go Live” button in the top right corner.
Carbon Black Live Response will drop you into C:\Windows\CarbonBlack\.
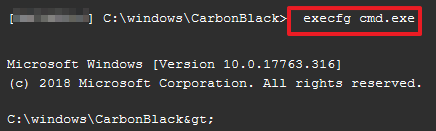
Type the following to execute cmd.exe, make the KAPE directory, move into the KAPE directory, and create a Targets directory on the suspect machine:
> exec cmd.exe
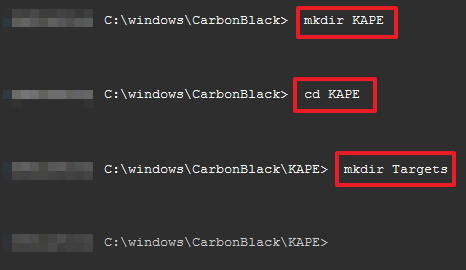
> mkdir KAPE
> cd KAPE
> mkdir Targets
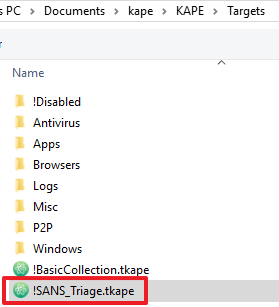
Move the kape.exe binary into C:\Windows\CarbonBlack\KAPE and the targets file (e.g. !SANS_Triage.tkape) into the C:\Windows\CarbonBlack\KAPE\Targets directory.
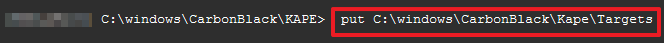
> put C:\Windows\CarbonBlack\KAPE
> put C:\Windows\CarbonBlack\KAPE\Targets
You’re ready to execute KAPE CLI. As a reminder, I recommend using the GUI version of KAPE to build your syntax.
> execfg .\kape.exe –tsource C: –tdest C:\Windows\CarbonBlack\KAPE\ –target !SANS_Triage –vhdx EXAMPLE
KAPE will take a few minutes to collect all the evidence. In the example below, it took 312 seconds to collect 2.5Gb of data. The part that takes some time is downloading the zipped VHDX. Alternatively, you could setup KAPE to send the evidence to an S3 bucket or FTP server.
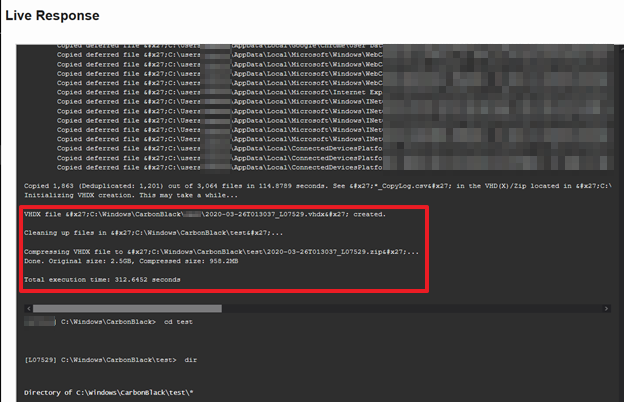
Once the evidence collection is done, download the evidence:
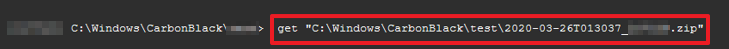
> get “C:\Windows\CarbonBlack\KAPE\example_file.zip”
Once you have the .zip file on your system and extracted, you’ll see a .vhdx file that can be mounted on a Windows 10+ system.
From here, you can use a forensic tool like AXIOM to parse the triage data or manually browse the data: