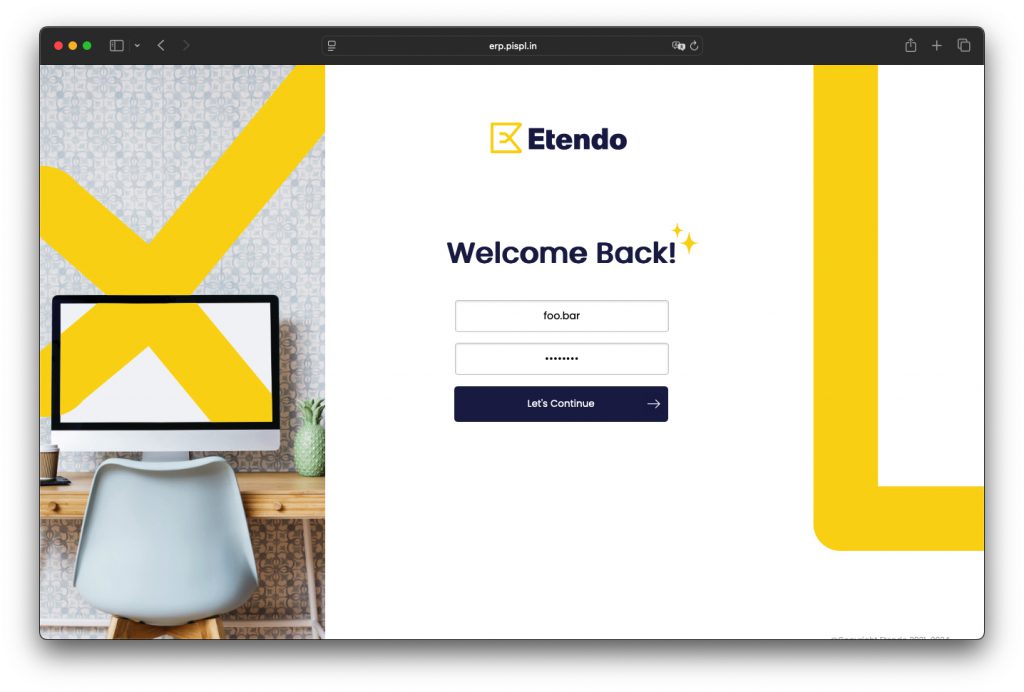
During a hunt for cleartext credentials in a client network searching for URL parameters matching to password=, pass=, psd=, etc., I discovered a url similar to: erp.pispl.in/openbravo/secureapp/loginhandler.html?user=foo.bar&password=May@2025 with the referrer of mpower.pispl.in/. The HTTP Request methods that exposed the username and password happened for both OPTIONS and POST.

Comments are closed.